Strengthening Cyber Resilience: Recovery Mechanisms and DR Strategies

Strengthening Cyber Resilience: Recovery Mechanisms and DR Strategies
Boosting Cyber Resilience: Recovery, BCP & DR Tactics to Meet RTO/RPO Targets and Ensure Business Continuity
- Authors
- Last Updated
- Tags
- Last Updated
- Authors
- Last Updated
- Tags
According to the 2025 Cisco Cybersecurity Index, only 4% of the organizations globally are said to have a mature cybersecurity readiness according. These are the companies that deployed advanced systems in the full spectrum of cybersecurity solutions effectively and are prepared to address any evolving threats. With the AI transformation and adoption moving at the speed of light, 89% of the 1500 Cybersecurity and IT professionals surveyed by Darktrace, believe that AI powered cyber threats will have a significant impact on their organizations in the near future.
Having cybersecurity measures is no longer enough as systems will fail, people will click on phishing emails and even the best-designed networks will be stress-tested by forces beyond control. That’s where cyber resilience framework steps into the picture. While cybersecurity primarily focuses on the prevention of unauthorized access, attacks and breaches by building strong defenses around systems, networks and databases, cyber resilience framework is a holistic approach. It involves preparing for, responding to, and recovering from disruptions, whether caused by cyberattacks, human error, or other adverse events to minimize downtime, financial loss, and reputational damage.
Fundamental Steps to Build Cyber Resilience
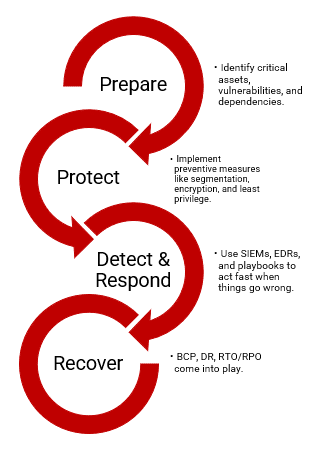
Recovery Mechanisms
Recovery mechanisms include technical and operational tools including redundancy systems that help resume normalcy after a disruption. While preventive controls are about avoidance, cyber recovery mechanisms are the safety net. It’s the ability to recover lost ground without compromising integrity or trust.
Recovery Strategies
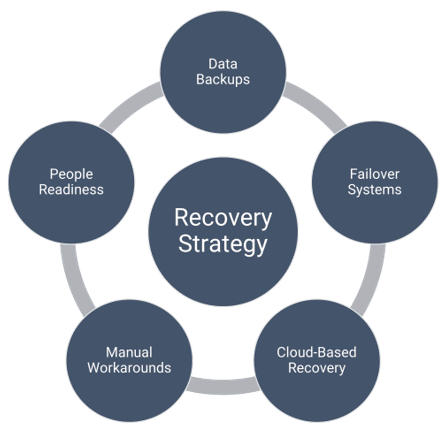
Data Backups
Data backups are the first line of defence against data loss. However, it’s important to understand the frequency and the method used for backups. One of the most popular backup strategies is the 3-2-1 strategy. Here, it involves keeping three copies of data, on two different media, with one copy stored offsite.

Related Read: SEBI CSCRF: Strengthening Organizational Security through Access Controls and Audit Logs
Three copies of data include primary production copy that is being actively used and two backup copies, in case of accidental deletion, corruption, or ransomware encrypting live data. Two different media include one on local disk and another on the cloud. This is to avoid a single point of hardware system failures. One copy stored offsite is either on a cloud backup, at another physical location, or remote server to protect against natural disasters, or localized fires/floods that can take out both production and onsite backup.
Failover Systems
Failover is to switch operations to a secondary system when the primary system fails. Failover systems can be put in place in three ways:
- Cold site: A physical office space with basic infrastructure (power, networking) but no pre-installed systems. In a disaster, hardware and backups are manually brought in. Small businesses and organizations tend to use cold site failover systems as it is cost effective.
- Warm site: An alternate cyber recovery location where the infrastructure is ready and the systems are pre-installed but not live. Data is synced periodically which allows faster activation as compared to cold sites. Warm sites are standard across Indian PSU banks, mandated under RBI’s BCP/DR policy guidelines.
- Hot site: A fully mirrored, always-on infrastructure with real-time data replication and automatic failover capabilities. For example, the National Stock Exchange operates a hot site in another city that runs in synchronous mode with its primary data centre, ensuring seamless continuity. SEBI mandates that critical systems switch within 2 hours, but NSE aims for near-zero downtime.
Cloud Disaster Recovery
These days most organisations use Cloud Disaster Recovery as a Service (DRaaS). Cloud platforms like AWS, Azure offer scalable backup storage, one-click disaster recovery and geographical redundancy.
Manual Workarounds
Even in the time of technology for every small task, a human in the loop remains essential. Printed SOPs for critical functions, manual transaction logging sheets and pre-authorized escalation protocols are essentials to put together a complete, cyber disaster recovery testing and mechanism.
People Readiness
Even the best plans fail without proper execution. And, for disaster recovery, it is vital for the incident response team to be prepared and trained for the actions to be taken. While updated call trees and emergency contacts secure crisis communication channels, disaster recovery testing and role-based responsibilities need to be a part of the cyber recovery toolkit.
Business Continuity Plans and DR Drills
A Business Continuity Plan (BCP) outlines how your organization will continue critical operations during and after a disruption highlighting its operational resilience.
The key elements of BCP include the following:
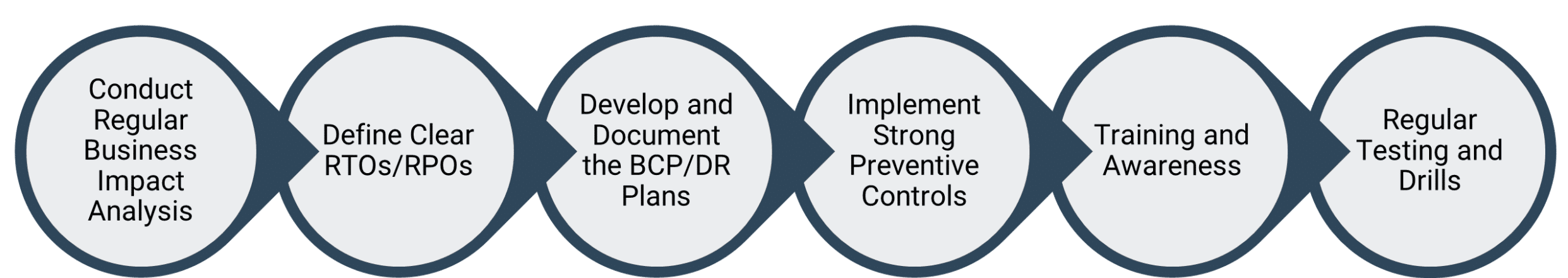
- Business Impact Analysis (BIA): Prioritise the assets that needs to recover first in case of a disaster, assess business’ critical processes, assets and dependencies. How would their downtime affect business. Based on this analysis, continuity strategies have to be created. Here is a ready reckoner for your reference:
Business Function Impact if Disrupted Maximum Acceptable Downtime (RTO) Maximum Data Loss Tolerated (RPO) Recovery Priority Core Banking System High financial & reputational loss 2 hours 15 minutes High Payroll Processing Employee dissatisfaction, compliance issues 24 hours 6 hours Medium Customer Support (CRM) Loss of trust, SLA breach 4 hours 1 hour High Email and Communication Internal disruption 8 hours 2 hours Medium Inventory Management Delay in dispatch, revenue loss 6 hours 2 hours Medium Public Website Brand visibility impact 12 hours 6 hours Low Compliance Reporting System Regulatory penalty 48 hours 12 hours Low - Business Continuity Strategies: Prepare strategies to keep essential functions running. This could involve alternate work sites, remote working capabilities, secondary suppliers, or manual workarounds.
- Documented Plans: Make clear procedures for emergency response, crisis management, and recovery of each critical function. Plans typically cover communication protocols, roles and responsibilities, and step-by-step recovery actions.
- Regular Testing and Updates: Test BCPs via drills or simulation exercises, ranging from natural disasters to cyberattacks, and update regularly to remain effective as the business changes.
How the IT sector in India dealt with the COVID-19 pandemic is one of the best examples to illustrate how important a solid BCP is. Companies quickly shifted to remote work and maintained operations with minimal disruption, enabling over 90% of their workforce to work from home securely within weeks, thus meeting client obligations despite nationwide lockdowns. This demonstrated how effective BCP implementation can ensure organizational resilience even in unprecedented scenarios.
Elements of Business Continuity Plans

Recovery Time Objectives and Recovery Point Objectives
Recovery Time Objective is the target maximum time to restore a service after a disruption. In simple words, Recovery Time Objective is the maximum time your systems can afford to be down. For a banking business, two hours would be an appropriate Recovery Time Objective, while for a website that generate leads, it could be longer.
Recovery Point Objective is the maximum acceptable data loss, the time interval of data that could be lost due to an incident. SEBI mandates a strict Recovery Point Objective of 15 minutes for critical operations. You would be able to assess the most appropriate Recovery Time Objective and Recovery Point Objective for your business based on the BIA.
Actions to Strengthen Cyber Resilience
The Bottom Line
Cyber resilience is no longer an option; it is now a requisite given the rapid technological adoption by organizations. In the prevalent threat landscape, businesses can safeguard data, trust and remain compliant by combining preventive defences, robust cyber recovery mechanisms, well-documented business continuity plans. The organizations that invest in IT resilience today will be the ones that thrive tomorrow, even in the face of inevitable disruptions.
Why Choose InCorp Global?
In today’s rapidly evolving digital landscape, ensuring cybersecurity and resilience is a cornerstone of trust. InCorp Global is your trusted partner in guiding through the complexities and provides a compliance roadmap backed by comprehensive cybersecurity services that fulfil all SEBI requirements. We are a full-fledged cyber security consulting company, having many years of experience in regulatory compliance. Our expert team along with security leads helps organizations perform gap assessment and quickly comply with the CSCRF controls.
Authored by:
Nikkitha K J | Cybersecurity
FAQ
Business Impact Analysis, Business Continuity Strategies, Plan Development, Training and Awareness and Testing & Maintenance are the five steps of a business continuity plan.
Preparing for cyberattacks requires proactive defence, backups, incident response plan, and an emergency response training while cyber recovery focuses on containment, restoration, and review.
A cyber-resilient BCP integrates cybersecurity, threat detection, asset mapping, strong governance, and adaptive testing.
Share
Share