Strengthening Cyber Resilience: Employee Awareness and Cyber Hygiene Training

Strengthening Cyber Resilience: Employee Awareness and Cyber Hygiene Training
Training Employees Against Threats: Why a Cyber-Aware Workforce Is Essential in Today’s Digital Age
- Authors
- Last Updated
- Tags
- Last Updated
- Tags
Share
Table of Contents
- Authors
- Last Updated
- Tags
Did you know that the global average cost of a data breach tied to employee carelessness was about $4.88 million in 2024? The current digital threat landscape is volatile. As the adoption of remote work, mobile device usage, and cloud-based services continues to grow, the attack surface for organizations continues to widen. Cyber attackers are now rapidly exploiting the gaps in employee awareness and cyber hygiene of organizations through phishing, ransomware, and other advanced persistent threats. According to the Cyber Security Outlook 2025 Report, one-third of the data breaches in India in 2024 involved AI-driven techniques.
This scenario makes it vital for organizations to be on toes with effective cyber hygiene practices including regular training, and heightened vigilance to safeguard sensitive data. SEBI’s Cyber Security and Cyber Resilience Framework outline several measures including phishing simulations and cyber hygiene for Regulated Entities to strengthen the overall cybersecurity posture.
Phishing and Phishing Simulation

Related Read: SEBI CSCRF: Strengthening Organizational Security through Access Controls and Audit Logs
Phishing is one of the most prominent types of cyberattack where criminals impersonate a bank, financial institution or a trustworthy entity to trick people into revealing sensitive information. This becomes an increasingly concerning issue when these attacks are targeted at employees in an organization.
One such instance is Operation RusticWeb. This was a sophisticated phishing campaign targeting Indian government personnel since October 2023, utilizing rust-based payloads and encrypted PowerShell commands. Similarly, in March 2024, Operation FlightNight, a cyber espionage campaign began with phishing emails containing decoy invitations from the Indian Air Force, targeting government entities and private energy companies. In the past few months, attackers are using AI-generated voice clones for ‘Deepfake Voice Phishing’ to impersonate trusted individuals, aiming to deceive targets into divulging sensitive information or transferring funds.
Types of Phishing
Phishing is no longer a one-size-fits-all scamming mechanism. What started as generic ‘lottery winner’ emails have now evolved into highly sophisticated, targeted attacks. Here are the most prominent types of phishing attacks.
- Email Phishing – This is one of the most common types of phishing. Attackers send bulk emails posing as trusted entities to steal data.
- Spear Phishing – This is a type of phishing that targets specific individuals or teams using personalized emails.
- Whaling – Similar to spear phishing, but here the attacks are aimed at senior executives and decision-makers.
- Clone Phishing – Attackers replicate a previously sent legitimate mail, attach malware or malicious links and resend it.
- Smishing (SMS Phishing) – Phishing through SMS or messaging apps.
- Vishing (Voice Phishing) – Attackers call victims pretending to be from a bank, government agency, or IT helpdesk. This has become more prevalent in the recent times using AI.
- Angler Phishing (Social Media Phishing) – Attackers create fake social media profiles impersonating customer support team of reputed organizations.
Recognizing these different phishing techniques arm employees with the awareness needed to stop attackers before they succeed.
Phishing in Organizations: The Current Situation and Solution
According to phishing-related data collected during CISA Assessments, a whopping 84% of the employees took the bait within first 10 minutes of receiving a malicious mail. These employees either interacted with the links or attachments within the mail or responded with sensitive information. Meanwhile, a meagre 13% of the employees reported the phishing attempts. The lack of employee awareness and cyber hygiene training is one the primary reasons for the same.
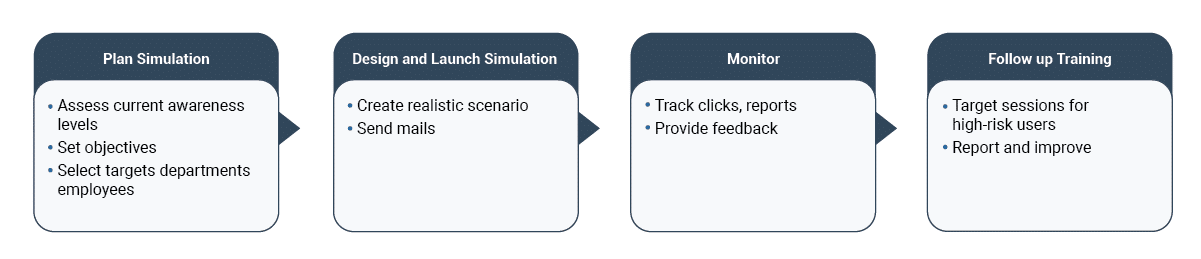
One of the ways to tackle this issue is to conduct phishing simulation. A phishing simulation is a controlled cybersecurity awareness training exercise where employees receive imitation phishing emails that mimic real ones. Instant feedback and additional phishing awareness training modules are sent to the employees who take the bait. These simulations are to be conducted at regular intervals to ensure training effectiveness.
Steps in Phishing Simulation Training
 Cyber Hygiene
Cyber Hygiene
While phishing simulation can help deal with one of the types of cyberattack, a proper cyber hygiene is a better approach to safeguarding digital assets, devices, and data. In simple terms, cyber hygiene is a set of best practices including regular patching, updating software, using strong passwords, and employee cybersecurity training.
Cyber Hygiene Checklist

1. Password Security
- Use strong, unique passwords for all accounts.
- Avoid reusing passwords.
- Change passwords regularly and do not share it on personal or work platforms.
- Implement multi-factor authentication.
2. Device and Data Protection
- Lock the screen when away from desk to ensure physical security.
- Use company-approved VPNs for remote work.
- Avoid accessing sensitive data on public Wi-Fi or unsecured networks.
- Encrypt sensitive data, both at rest and in transit.
- A spam filtering policy should be configured in available tools as a precaution.
3. Software Updates and Patch Management
- Keep operating systems, browsers, applications, and antivirus software updated promptly.
- Enable automatic updates.
4. Access Controls
- Restrict access rights based on job role and responsibilities.
- Regularly review and audit access logs for suspicious patterns.
5. Data Backup and Recovery
- Back up critical files regularly, preferably daily for essential data.
- Store backups securely offsite or in the cloud and test data recovery procedures.
6. Network Security
- Use firewalls, intrusion detection and prevention systems.
- Secure routers and Wi-Fi by changing default settings and enabling encryption.
7. Mandatory Cybersecurity Training and Awareness for Employees
- Conduct cybersecurity awareness and phishing simulation training periodically.
- Encourage immediately reporting of suspicious emails, messages, or activities.
- Educate everyone on data handling, physical security, safe use of mobile devices, and other security protocols.
8. Incident Response and Monitoring
- Draft an incident response plan and update it regularly.
- Monitor systems in real time basis using automated phishing detection tools.
- Proactively monitor the cyberspace to identify phishing websites related to the organization’s domains and report to CSIRT-Fin/CERT-In.
9. Remote Working Security and Mobile Device Security
Ensure remote working security policies are established and regularly reviewed.
- Mandate mobile device security tools and configurations for all remote devices.
- Conduct periodic risk assessments of remote access points.
10. Compliance and Risk Management
- Comply with regulatory requirements like GDPR and industry standards.
- Conduct regular risk assessments and vendor reviews.
- Educate stakeholders about cybersecurity risks, including the downside of sharing login credentials/passwords/OTP.
The Bottom Line
Digital hygiene is now a critical necessity given the heavy reliance technology and digital assets, software and tools. Regular phishing simulations, documented security protocols and overall cybersecurity training enhance employees’ ability to detect and respond to attacks. Cybersecurity is a huge responsibility for organizations today. Investing in employee cybersecurity training is the first line of defence in building resilient, secure enterprises.
Why Choose InCorp Global?
In today’s rapidly evolving digital landscape, ensuring cybersecurity and resilience is a cornerstone of trust. InCorp Global is your trusted partner in guiding through the complexities and provides a compliance roadmap backed by comprehensive cybersecurity services that fulfil all SEBI requirements. We are a full-fledged cyber security consulting company, having many years of experience in regulatory compliance. Our expert team along with security leads helps organizations perform gap assessment and quickly comply with the CSCRF controls. To learn more about our services, you can write to us at info@incorpadvisory.in or reach out to us at (+91) 77380 66622.
Authored by:
Nikkitha K J | Cybersecurity
FAQs
Phishing simulation training is a method to create awareness among employees about phishing and train them to detect and report when they receive malicious mails.
Cyber hygiene sets the basic practices to follow to keep the digital assets and data of the organization secure. Since many breaches are usually a result of human error and weak security habits, maintaining strong cyber hygiene minimizes the risk of breaches.
Phishing training simulations expose employees to phishing in a controlled environment. These help the employees recognize suspicious emails, links, and tactics used by attackers. Thus, they detect and report actual phishing attacks promptly.
Share
Share